End to End CI/CD Jenkins Pipeline Project using SonarQube, OWASP Dependency Check and Docker
DevOps Blog: 3
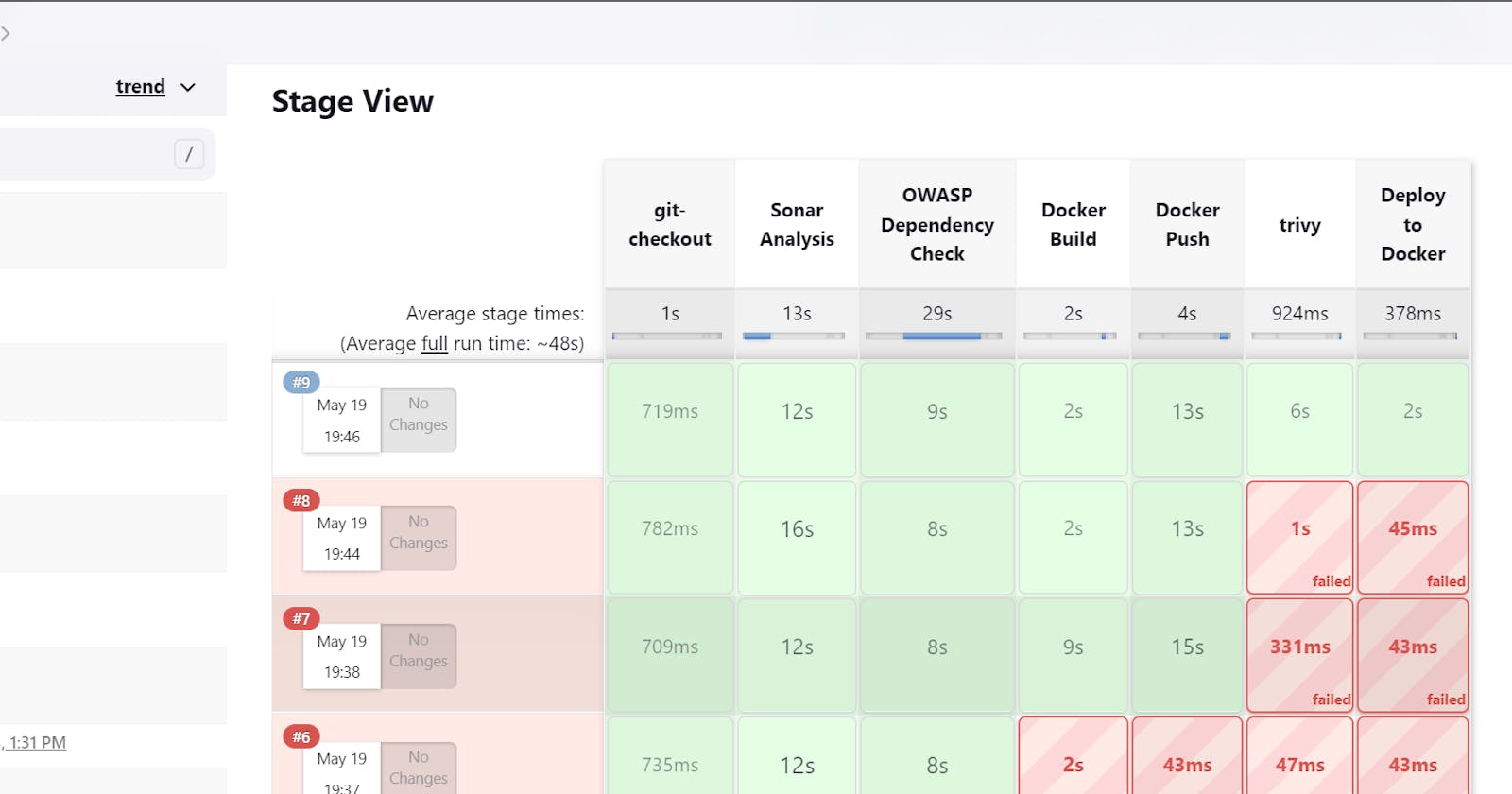
Here we see How to create End to End CI/CD pipeline project using Jenkins
The project involves using Git, SonarQube, OWASP Dependency Check, Trivy, and Docker in combination with Jenkins to push and deploy a Docker container. Here's a breakdown of each component:
Git: Git is a distributed version control system used for tracking changes in source code. It allows multiple developers to collaborate on a project and manage different versions of the codebase.
SonarQube: SonarQube is a code quality management platform that provides continuous inspection of your code. It analyzes code for bugs, vulnerabilities, and code smells, and provides detailed reports to help maintain code quality.
OWASP Dependency Check: OWASP Dependency Check is a tool that identifies known vulnerabilities in project dependencies. It scans the project's dependencies and checks against a database of known security vulnerabilities to ensure that no vulnerable components are being used.
Trivy: Trivy is a container vulnerability scanner. It scans container images and reports any known vulnerabilities in the software packages installed within the image. Trivy helps ensure that the deployed Docker container is free from known security issues.
Docker: Docker is a containerization platform that allows you to package an application and its dependencies into a lightweight, portable container. Docker containers provide an isolated and consistent environment for running applications.
Jenkins: Jenkins is an open-source automation server that enables continuous integration and continuous delivery (CI/CD). It allows you to automate the building, testing, and deployment processes. Jenkins can be configured to trigger the necessary steps when changes are pushed to the Git repository.
In this project, you would typically set up a Jenkins job that performs the following steps:
Fetch the source code from the Git repository.
Run SonarQube analysis on the codebase to identify any code quality issues.
Execute OWASP Dependency Check to scan the project's dependencies for vulnerabilities.
Use Trivy to scan the Docker image for any known security vulnerabilities.
Build the Docker image, including the necessary dependencies and application code.
Push the Docker image to a Docker registry, such as Docker Hub or a private registry.
Deploy the Docker image to a Docker container, either on a local or remote server, using Docker commands or a container orchestration tool like Kubernetes.
By integrating these tools and processes into a Jenkins pipeline, you can automate the build, test, and deployment of your application in a secure and efficient manner.
I sincerely hope that this project will benefit you and improve your resume. We appreciate you reading the article. If you find my blogs educational and entertaining, kindly like and follow. Let's grow and learn together:) - Nitesh Singh